Lead2pass Offering Free 70-346 Dumps Files For Free Downloading By 70-346 Exam Candidates:
https://www.lead2pass.com/70-346.html
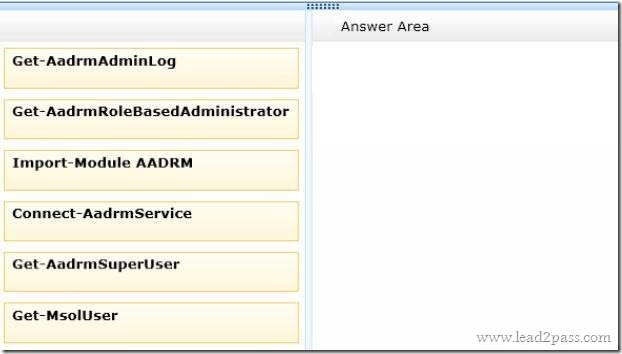
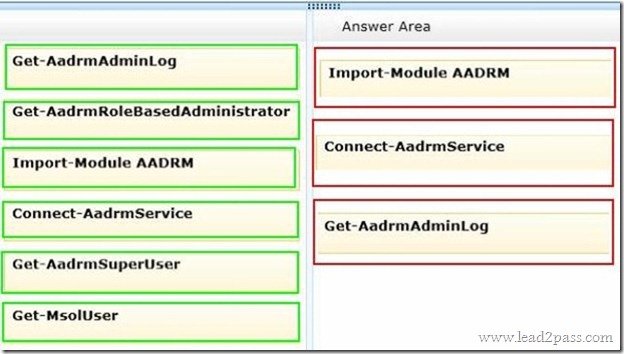
QUESTION 31
Drag and Drop Question
You are the Office 365 administrator for your company.
You audit the Windows Azure Active Directory Rights Management configuration for the company.
You need to view a log of the recent administrative commands performed against the Microsoft Rights Management Service.
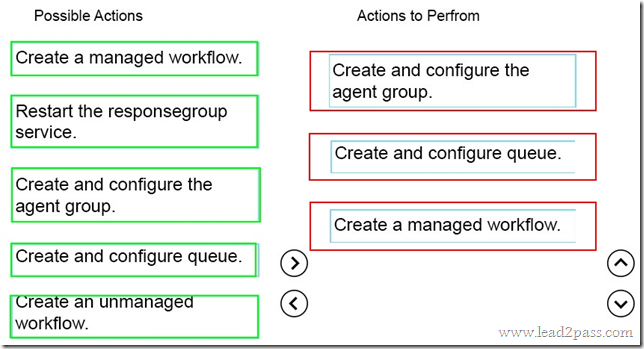
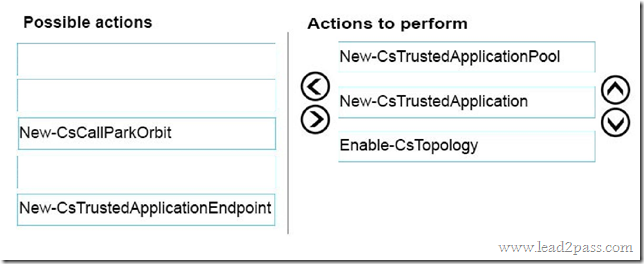
Which three Windows PowerShell cmdlets should you run in sequence? To answer, move the appropriate cmdlets from the list of actions to the answer area and arrange them in the correct order
Answer:
QUESTION 32
Your company has an Office 365 subscription.
The network contains an Active Directory domain.
You configure single sign-on for all users.
You need to verify that single sign-on functions for the users who access Office 365 from the Internet.
What should you run?
A. the Get-MSOLFederationProperty cmdlet
B. the Test-OrganizationRelationship cmdlet
C. the Microsoft Remote Connectivity Analyzer
D. the Microsoft Exchange Server Deployment Assistant
Answer: C
QUESTION 33
You are the administrator for a company named Contoso, Ltd.
The company has an Office 365 subscription.
Your need to prevent users from changing their user display name by using Outlook Web App. What should you do?
A. Run the Set-MsolCompanyContactInformation cmdlet.
B. Modify the default email address policy.
C. Run the Set-MsolUserPrincipalName cmdlet.
D. Modify the default role assignment policy.
Answer: D
Explanation:
http://help.outlook.com/en-us/140/ff852817.aspx
QUESTION 34
You are the Office 365 administrator for your company. The company uses Active Directory Federation Services (AD FS) to provide single sign-on to cloud-based services.
You enable multi- factor authentication.
Users must NOT be required to use multi-factor authentication when they sign in from the company’s main office location. However, users must be required to verify their identity with a password and token when they access resources from remote locations.
You need to configure the environment.
What should you do?
A. Disable AD FS multi-factor authentication.
B. Configure an IP blacklist for the main office location.
C. Disable the AD FS proxy.
D. Configure an IP whitelist for the main office location.
Answer: D
Explanation:
https://msdn.microsoft.com/en-us/library/azure/dn807156.aspx
The Trusted IPs allows users to bypass Azure Multi-Factor Authentication for website requests originating from specific IP addresses or subnets. For example, you may want to exempt users from Azure Multi-Factor Authentication while logging in from the office. For this, you would specify the office subnet as an Trusted IPs entry. To configure Trusted IPs use the following procedure: bla bla bla :))
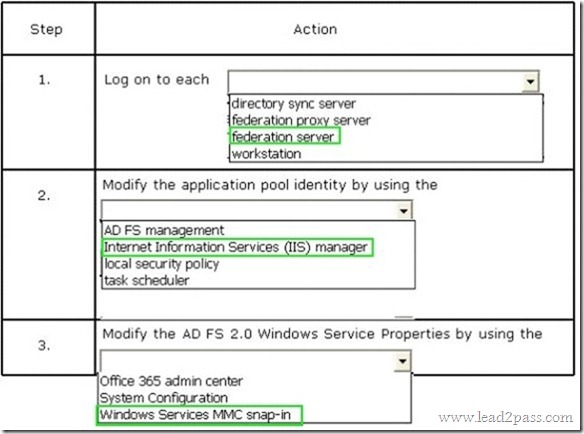
QUESTION 35
Hotspot Question
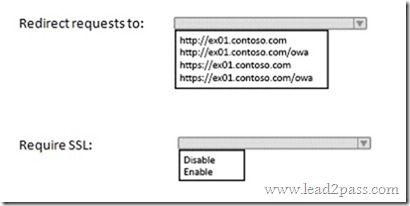
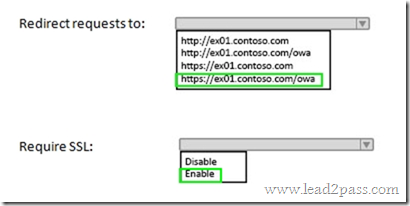
An organization has over 10,000 users and uses a SQL-based Active Directory Federation Services (AD FS) server farm.
You need to change the AD FS 2.0 service account password.
What should you do? Select the correct answer from each list in the answer area.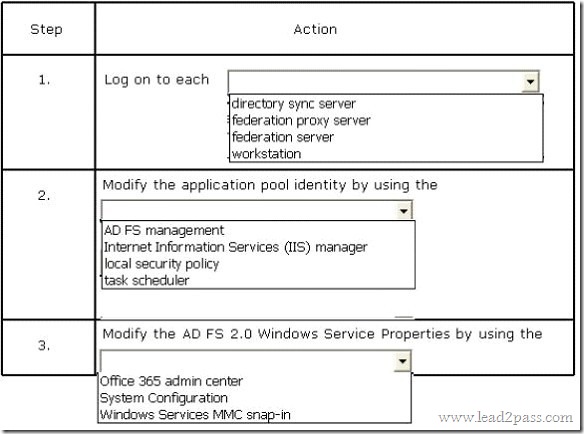
Answer:
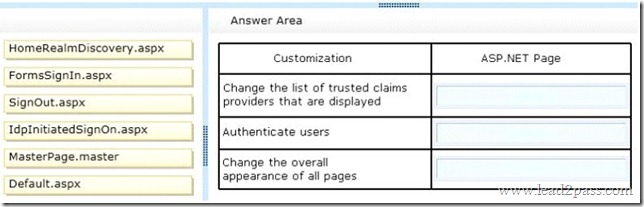
QUESTION 36
Drag and Drop Question
A company deploys an Office 365 tenant.
You install the Active Directory Federation Services (AD FS) server role on a server that runs Windows Server 2012.
You install and configure the Federation Service Proxy role service.
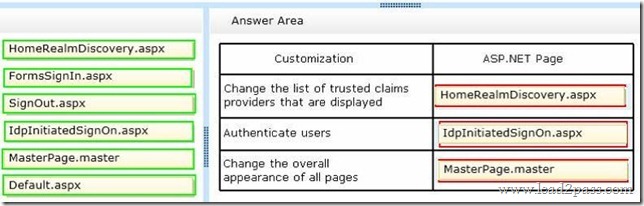
Users sign in by using the Security Assertion Markup Language (SAML) protocol.
You need to customize the sign-in pages for Office 365.
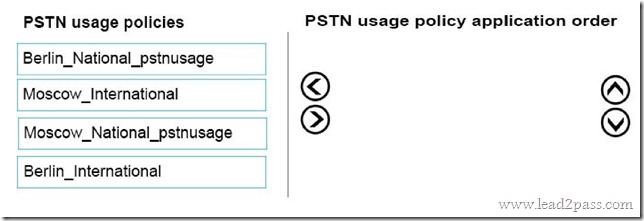
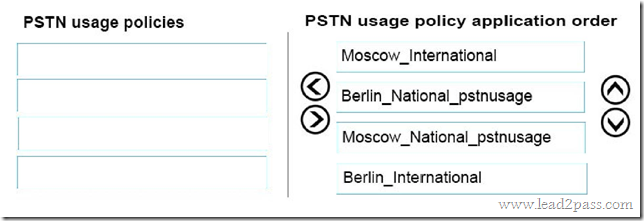
Which pages should you customize? To answer, drag the appropriate page to the correct customization. Each page may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Answer:
QUESTION 37
Contoso uses Office 365 for collaboration services.
You implement single sign-on (SSO) with Office 365 by using Active Directory Federation Services (AD FS).
You need to implement Windows Azure multi-factor authentication.
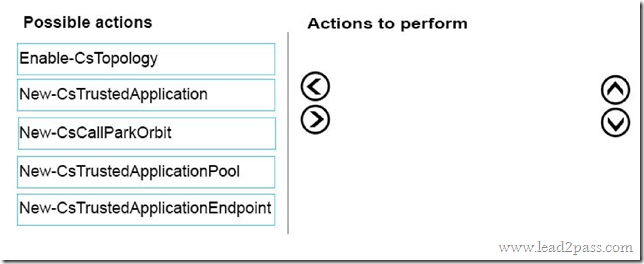
Which three actions should you perform? Each correct answer presents part of the solution.
A. On the AD FS federation server, run PhoneFactorAgentSetup.exe.
B. On the AD FS Federation server, run WindowsAzureSDK-x64.exe.
C. On the AD FS Federation server, run the Windows PowerShell cmdlet Register-AdfsAuthenticationProvider.
D. On the AD FS Federation server, run FsConfigWizard.exe.
E. Run the Active Directory Domains and Trusts MMC snap-in. Register Windows Azure Multi-Factor
Authentication Server as an additional authentication provider.
F. Run the Windows Azure Multi-Factor Authentication Server Authentication Configuration Wizard.
Answer: BCF
Explanation:
http://blogs.technet.com/b/cbernier/archive/2013/12/02/multi-factor-authentication-the-simple-way.aspx
QUESTION 38
A company plans to deploy an Office 365 tenant.
You have two servers named FS1 and FS2 that have the Federation Service Proxy role service installed.
You must deploy Active Directory Federation Services (AD FS) on Windows Server 2012.
You need to configure name resolution for FS1 and FS2.
What should you do?
A. On FS1 and FS2, add the cluster DNS name and IP address of the federation server farm to the
hosts file.
B. On FS1 only, add the cluster DNS name and IP address of the federation server farm to the hosts file.
C. On FS1 only, add the cluster NetBIOS name and IP address of the federation server farm to the
LMHOSTS file.
D. On FS1 and FS2, add the cluster NetBIOS name and IP address of the federation server farm to the
LMHOSTS file.
Answer: A
Explanation:
http://office365support.ca/setting-up-adfs-proxy-server-part-1/
70-346 dumps full version (PDF&VCE): https://www.lead2pass.com/70-346.html
Large amount of free 70-346 exam questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDVjBwLTI5aDNwM1k
You may also need:
70-347 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDTmZ1RjZSYlV3V00